Transitioning to DevOps requires a change in culture and mindset. In simple words, DevOps means removing the barriers between traditionally siloed teams: development and operations. In some organizations, there may not even be a separation between development, operations and security teams; engineers are often required to do a bit of all. With DevOps, the two disciplines work together to optimize both the productivity of developers and the reliability of operations.
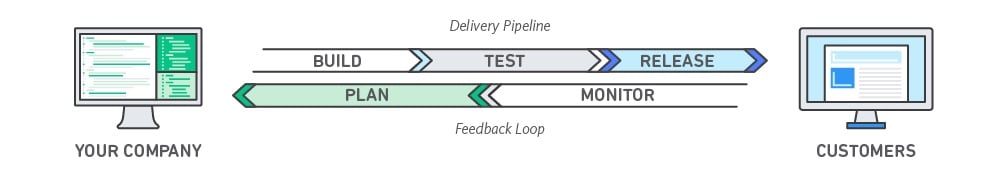
The alignment of development and operations teams has made it possible to build customized software and business functions quicker than before, but security teams continue to be left out of the DevOps conversation. In a lot of organizations, security is still viewed as or operates as roadblocks to rapid development or operational implementations, slowing down production code pushes. As a result, security processes are ignored or missed as the DevOps teams view them as an interference toward their pending success. As part of your organization strategy towards a security, automated and orchestrated cloud deployment and operations - you will need to unite the DevOps and SecOps teams in an effort to fully support and operationalize your organizations cloud operations.
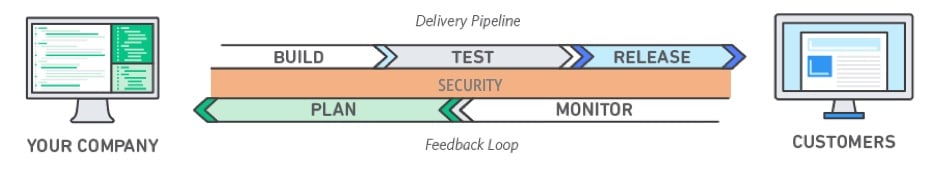
A new word is here, DevSecOps
Security teams tend to be an order of magnitude smaller than developer teams. The goal of DevSecOps is to go from security being the “department of no” to security being an enabler.
“The purpose and intent of DevSecOps is to build on the mindset that everyone is responsible for security with the goal of safely distributing security decisions at speed and scale to those who hold the highest level of context without sacrificing the safety required,” describes Shannon Lietz, co-author of the “DevSecOps Manifesto.”
DevSecOps refers to the integration of security practices into a DevOps software delivery model. Its foundation is a culture where development and operations are enabled through process and tooling to take part in a shared responsibility for delivering secure software.
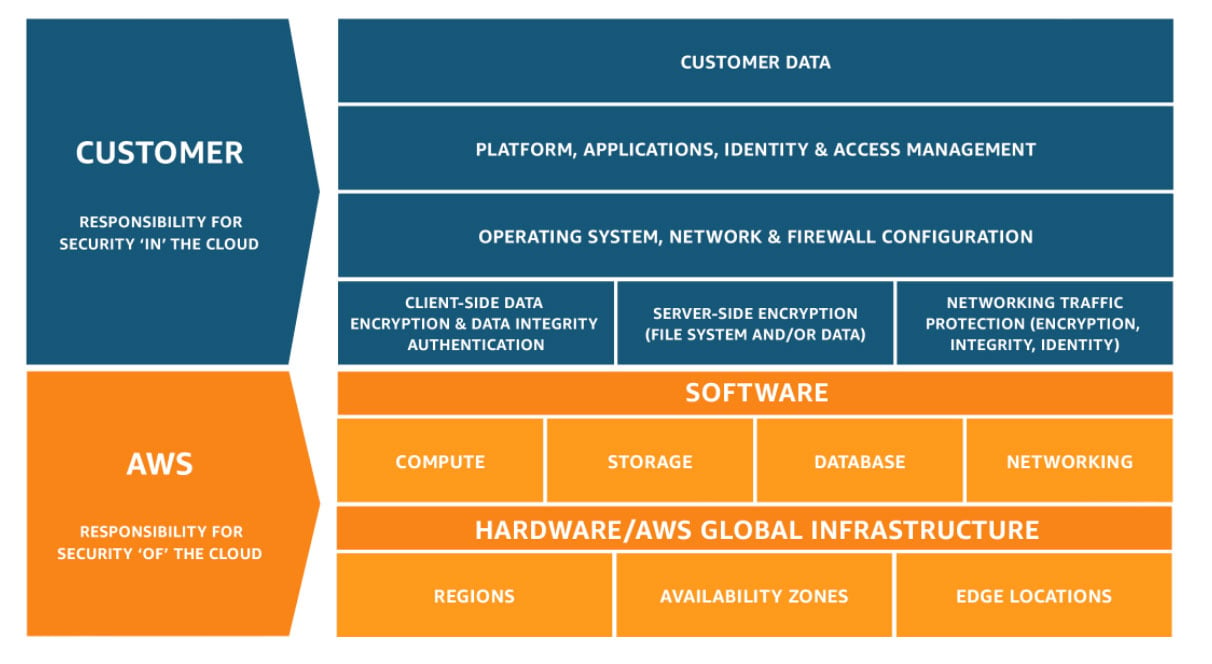
For example, if we take a look on the AWS Shared responsibility Model, we see that us as a customer of AWS have a lot of responsibility in securing our environment. We cannot expect someone to do that job for us.
The definition of DevSecOps Model, is to integrate security objectives as early as possible in the lifecycle of software development. While security is “everyone’s responsibility,” DevOps teams are uniquely positioned at the intersection of development and operations, empowered to apply security in both breadth and depth.
Nowadays, scanners and reports simply don't cover the whole picture. As part of the testing that is done in a pipeline, the devsecops adds a penetration test to validate that the new code is not vulnerable and our application stays secure.
Organizations can not wait to fall victim to mistakes and attackers. The security world is changing, devsecops teams are leaning in over saying “No”, nor open to hear and work with Open Contribution & Collaboration over Security-Only Requirements.
Best practices for DevSecOps
DevSecOps should be the natural incorporation of security controls into your development, delivery, and operational processes.
Shift Left
DevSecOps are moving engineers towards security from the right (at the end) to the left (beginning) of the Development and Delivery process. In a DevSecOps environment, security is an integral part of the development process from the get go. An organization that uses DevSecOps brings in their cybersecurity architects and engineers as part of the development team. Their job is to ensure every component, and every configuration item in the stack is patched, configured securely, and documented.
Shifting left allows the DevSecOps team to identify security risks and exposures early and ensure that these security threats are addressed immediately. Not only is the development team thinking about building the product efficiently, but they are also implementing security as they build it.
Automated Tests
The DevOps Pipeline performs several tests and checks for the code before the code deploys to production workloads, so why not add security tests such as static code analysis and penetrations tests? The key concept here is to understand that passing a security test is as important as passing a unit test. The pipeline will fail if a major vulnerability will be found.
Slow Is Pro
A common mistake is to deploy several security tools at once such as AWS config for compliance and a SAST (Static application security testing) tool for code analysis, or deploy one tool with a lot of tests and checks. This method only creates an extra load of problems for developers which slows the CI/CD process and is not very agile. Instead, when an organization is implementing tools like those mentioned above they should start with a small set of checks which will slowly get everybody on board and get the developers used so that they’re code is tested.
Keep It A Secret
“Secrets” in Information Security often means all private information a team should know such as API Keys, Passwords, Databases connection strings, SSL certificates etc. Secrets should be kept in a safe place and not hard coded in a repo for example. Another issue is to keep the secret rotated and generate new ones every once in a while. A compromised access key can cause devastating results and major business impact, constantly rotating these keys is a mechanism determined to protect against old secrets being missly used. There are a lot of great tools for these purposes such as Keepass, AWS Secret manager or Azure Key Vault.
Security education
Security is a combination of engineering and compliance. Organizations should form an alliance between the development engineers, operations teams, and compliance teams to ensure everyone in the organization understands the company's security posture and follows the same standards.
Everyone involved with the delivery process should be familiar with the basic principles of application security, the Open Web Application Security Project (OWASP) top 10, application security testing, and other security engineering practices. Developers need to understand thread models, compliance checks, and have a working knowledge of how to measure risks, exposure, and implement security controls
At Cloudride, we live and breathe cloud security, and have supported numerous organizations in the transition to the DevSecOps model. From AWS, MS Azure, and other ISV’s, we can help you migrate to the cloud faster yet securely, strengthen your security posture and maximize business value from the cloud.
Check out more information on the topic here, and Book a free consultation call today here!


